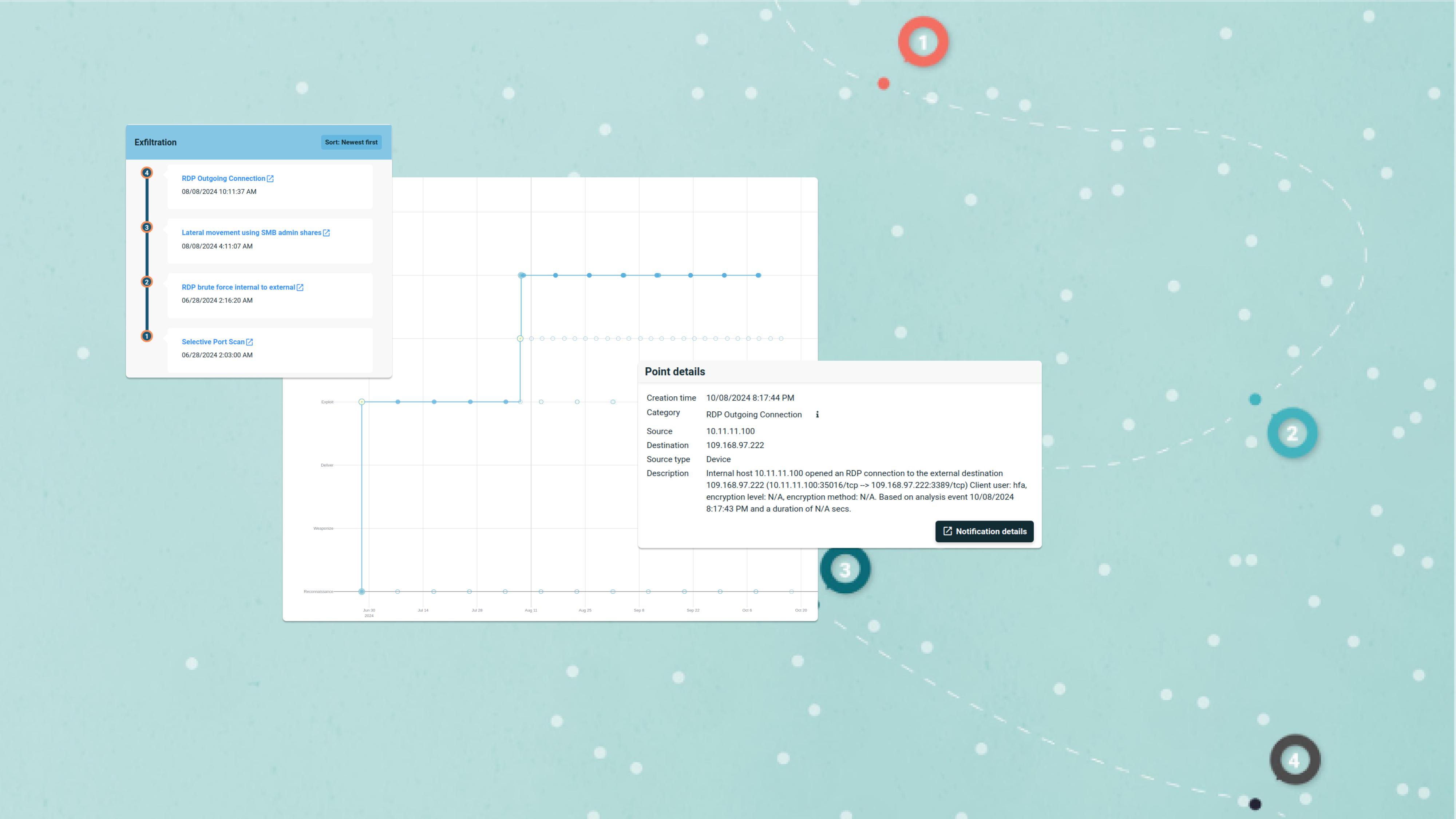
A New Risk Profile: The Critical Challenge of AI Security
The era of rapid AI development, also known as the AI Spring, is pressuring companies to shorten their Time-to-Market drastically. In order to stay competitive, they rush to release AI-based products, often sacrificing thorough development and testing. This rush results in underdeveloped AI systems that lack robustness and reliability. New machine learning (ML) algorithms, which are crucial to these developments, may enter production without adequate large-scale review, increasing the risk of ineffective or potentially hazardous implementations. The lack of software development resources increases these risks and challenges even further. Today’s high demand for AI expertise significantly outweighs the supply of skilled professionals and the high costs of computational resources, like GPUs, reduces the general access to AI models. The situation gets even trickier because of data quality, where training data does not meet the expectation and need for high-quality and relevance, resulting in weak AI outputs.