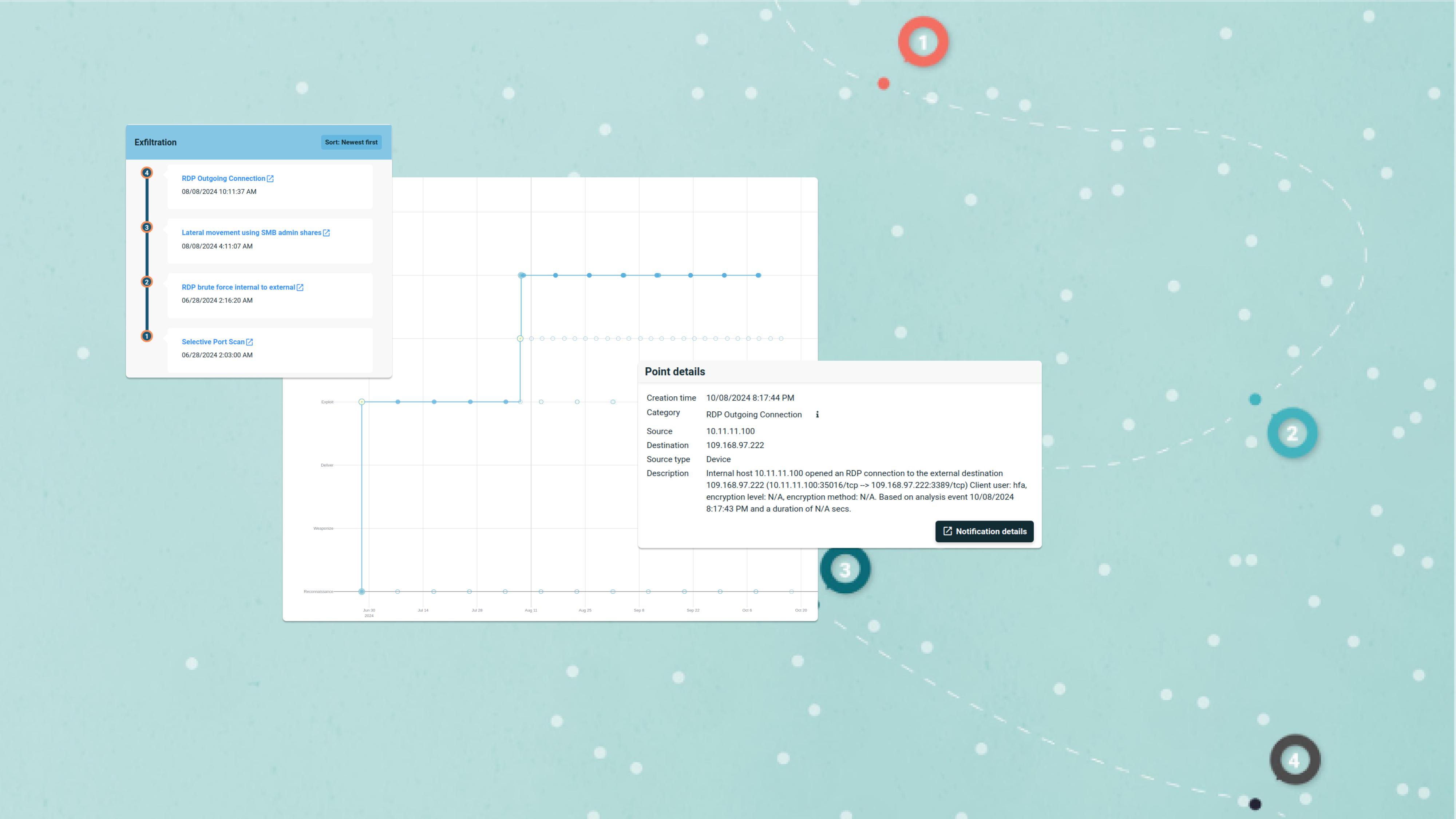
Why People, Not Just Hackers, Are Your Biggest Cybersecurity Risk
In a time where data is as valuable as gold, the frequency of data breaches has become a concerning reality. While advanced hacking methods get more media attention, organizations are ramping up their cybersecurity measures. These measures often include evaluating system vulnerabilities, fortifying firewalls, scrutinizing email security, and optimizing identity and access management. However, one crucial component of the attack surface is frequently neglected: the human element. This oversight has led to a surge in threat actors exploiting human vulnerabilities, making it a top method for initial access into systems.