What We Learned from the ISO 42001 Webinar
AI is reshaping how we operate, but as innovation accelerates, so does scrutiny. That’s why our recent webinar, “Securing and Demonstrating AI Compliance with ISO 42001”, was so timely.
Posts about:
-Jul-25-2025-03-00-49-7281-PM.jpg)
AI is reshaping how we operate, but as innovation accelerates, so does scrutiny. That’s why our recent webinar, “Securing and Demonstrating AI Compliance with ISO 42001”, was so timely.

The grandparent scam, also known as the "grandchild in distress" scam, is a type of fraud that preys on the emotions of older individuals. While it may not specifically be labeled as a "cybersecurity" scam, it often involves the use of technology to carry out the deception. Here's how the grandparent scam typically works:
Initial Contact: Scammers often initiate contact with the victim through a phone call. They may claim to be a grandchild or someone else the grandparent cares about. In some cases, they might have obtained personal information about the family through social media or other online sources.
Urgent Situation: The scammer will fabricate a story about being in some kind of trouble or emergency situation, such as being arrested, in a car accident, or facing a medical emergency. The goal is to create a sense of urgency and panic.
Request for Money: After establishing the emergency scenario, the scammer will request immediate financial assistance. They might ask the grandparent to wire money, send gift cards, or provide credit card information to help them out of their supposed predicament.
Emotional Manipulation: The scammer relies on the grandparent's emotions, creating a sense of urgency and fear that their grandchild is in danger. This emotional manipulation makes it more likely that the victim will act quickly without verifying the situation.
Preventing Verification: To avoid detection, the scammer may insist that the grandparent not contact other family members to verify the situation. They might claim that they are embarrassed or don't want others to know about their predicament.
Loss of Money: Once the grandparent sends money or provides financial information, it becomes nearly impossible to recover the funds. Scammers may disappear, change phone numbers, or use other tactics to avoid being traced.
To protect against such scams:
Verify the Story: Always verify the caller's identity by asking questions that only your actual grandchild would know. Contact other family members to confirm the situation.
Never Send Money Without Verification: Be skeptical of urgent requests for money and never send money without independently verifying the emergency.
Report Suspicious Activity: If you suspect a scam, report it to local law enforcement and relevant authorities. They can provide guidance on how to proceed.
Educate Seniors: Inform older family members about common scams and encourage them to be cautious about unsolicited calls or messages requesting money.
Remember that scammers constantly adapt their tactics, so it's essential to stay informed and vigilant to protect against various types of scams, including those targeting vulnerable populations like grandparents.

During the holidays, several cybersecurity topics become particularly relevant due to the increased online activity and potential risks. Digital gift card scams are one of these topics and unfortunately common during the holiday season, as scammers take advantage of people's generosity and the increased use of gift cards as presents. Here are some digital gift card scams to be aware of:

As the Holidays approach, there is an increasing popularity of finishing gift shopping for friends and family via the convenience of online shopping. And now with so many vendors offering the convenience of affordable shipping, the demand for online shopping has risen even more! Cybercriminals often take advantage of events and holidays to exploit vulnerabilities. During the holiday season, as online shopping continues to grow in popularity, cybersecurity awareness is crucial to protect individuals and organizations from various online threats. Here are some online shopping safety tips for maintaining cybersecurity awareness during online shopping:


Protecting PII or personally identifiable information is paramount in ensuring compliance and protecting against data breaches.

Securing your organization's network infrastructure requires keeping one step ahead. Otherwise, remediating network security issues can be very expensive. That's where a SOC 2 Readiness Assessment comes in.
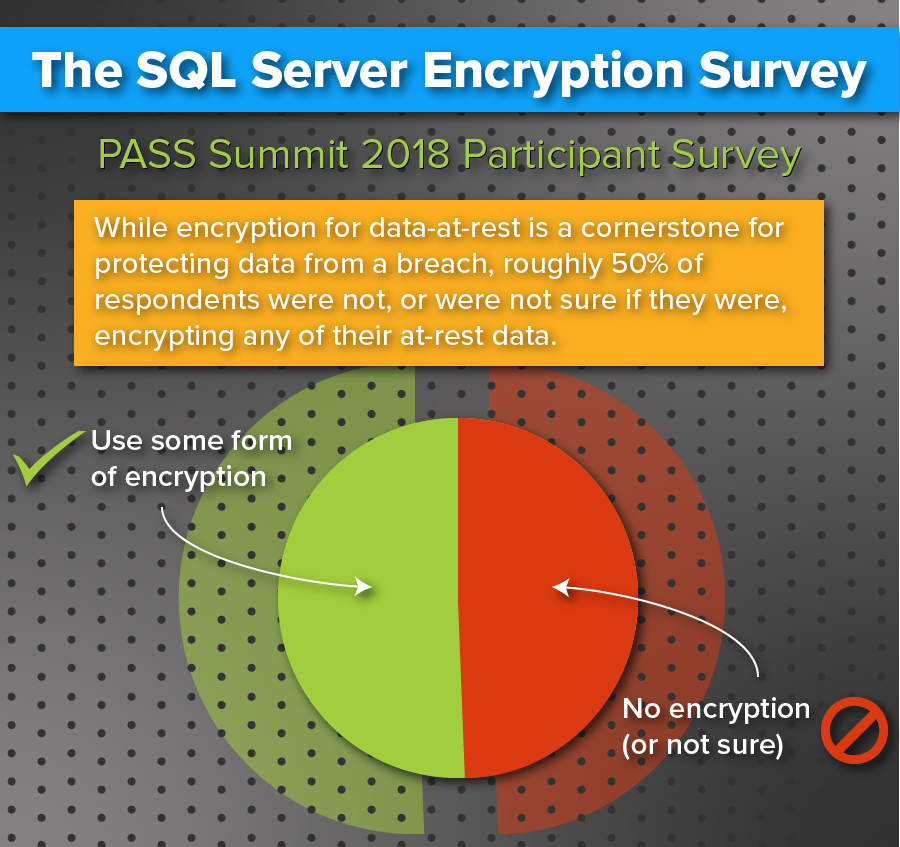
In 2018, Townsend Security had a chance to participate in the 20th annual PASS Summit in Seattle as an exhibitor. While there, they had an opportunity to ask attendees about their company's encryption and key management practices. Our own Tim Roncevich was able to review the results and give his expert opinion on some of the findings.
In total, 93 people participated in the survey.
Here are some key findings:
-1.jpg)
Effective December 15, 2018, all SOC 2 audits now need to comply with TSP Section 100—the 2017 Trust Services Criteria for security, availability, processing integrity, confidentiality, and privacy, building upon the COSO framework.
The new SOC 2 audit reports will focus on changes meant to address head-on the current security breach landscape, which appears to be getting worse with each incident.
Many of these changes align with the 2013 Committee of Sponsoring Organizations of the Treadway Commission (COSO) Internal Control criteria already in place but feature tighter controls to thwart and mitigate cybersecurity breaches and increase flexibility in the application of controls over areas such as security and privacy. The new framework affects those service organizations which will be issuing SOC 2 and/or SOC 3 reports with reporting periods ending after December 15, 2018. Companies, who did not early adopt the new standard, will need to prepare for examinations of their controls under the new Trust Services Criteria, which aligns with the new COSO framework.
The new points of focus include:
Security: The effectiveness of policies and procedures governing the way organizations protect themselves against unauthorized access and respond to security breaches resulting in unauthorized disclosure of information will be periodically evaluated.
Availability: Information and systems must be available for operation and use to meet the entity’s objectives.
Confidentiality: Information designated as confidential must be sufficiently protected from unauthorized access to meet organizational effectiveness.
Processing Integrity: System processing should be complete, valid, accurate, timely, and authorized to meet organizational objectives.
Privacy: Personally identifiable information must be collected, used, disclosed, and disposed of in a secure manner.
What Are the Main Implications?
The primary implications of these changes include positive impact on reporting clarity as a result of a defined level of transparency between service organizations and their users. Adding to the positive impact of the new framework, the detailed and thorough audits will be more satisfactory to service organization's clients and assessors. For service organizations, the revisions issued over the past 15 months represent new compliance challenges, which require additional controls, as well as additional effort preparing the system description.
The main principles guiding the 2013 COSO Internal Control–Integrated Framework are comprehensive and are outlined here:
Your organization should demonstrate a commitment to integrity and ethical values. This starts with the board of directors ensuring oversight over management and performance of internal controls.
Management, in turn, should work closely with the board of directors in pursuit of organizational objectives, which include the commitment to attract, develop, and retain competent staff and hold employees accountable for their internal-control responsibilities.
Your organization must not only identify and assess risks with sufficient clarity but also analyze those risks as a basis for how risks should be managed when they arise.
In other words, have a well-thought-out plan of action.
Your organization should also consider the potential for fraud in assessing risks to ensure the integrity of the process and identify changes, which could significantly affect the system of internal control―a fail-safe measure.
Your institution must select and develop control activities, which contribute to the mitigation of risk to the achievement of your goals to acceptable levels. Basically, you need to select processes for governing technology, which support your objectives, and you should deploy policies and procedures to establish expected outcomes.
Governments and other related entities rely on information gathering to support their activities. Your organization is no different when it comes to meeting the new SOC 2 audit requirements.
You will need to obtain and use relevant, quality information to support the functioning of internal control. In addition, it is essential to effectively communicate any information internally and externally―perhaps with third parties―regarding matters, which affect the functioning of internal control. In other words, all parties must talk to each other.
Compliance is a function of how well you self-monitor your own activities. Your organization is expected to select, develop, and perform ongoing evaluations of the effectiveness of each component of internal control and its functional efficiency.
If an internal control deficiency is identified, you are expected to communicate your findings to all parties responsible for taking corrective action, including C-suite executives, the board of directors, and other decision makers.
As the cybersecurity landscape evolves, compliance becomes a constantly moving target, which often brings with it confusion over how to remain compliant.
With such major changes coming your way, you may need to consider a Readiness Assessment to update your compliance program to align with the new Trust Services Criteria.
.jpg)
Securing sensitive customer information is paramount in ensuring compliance and protecting against data breaches.