The Long-Awaited Upgrade: NIS2 and what it means for cybersecurity
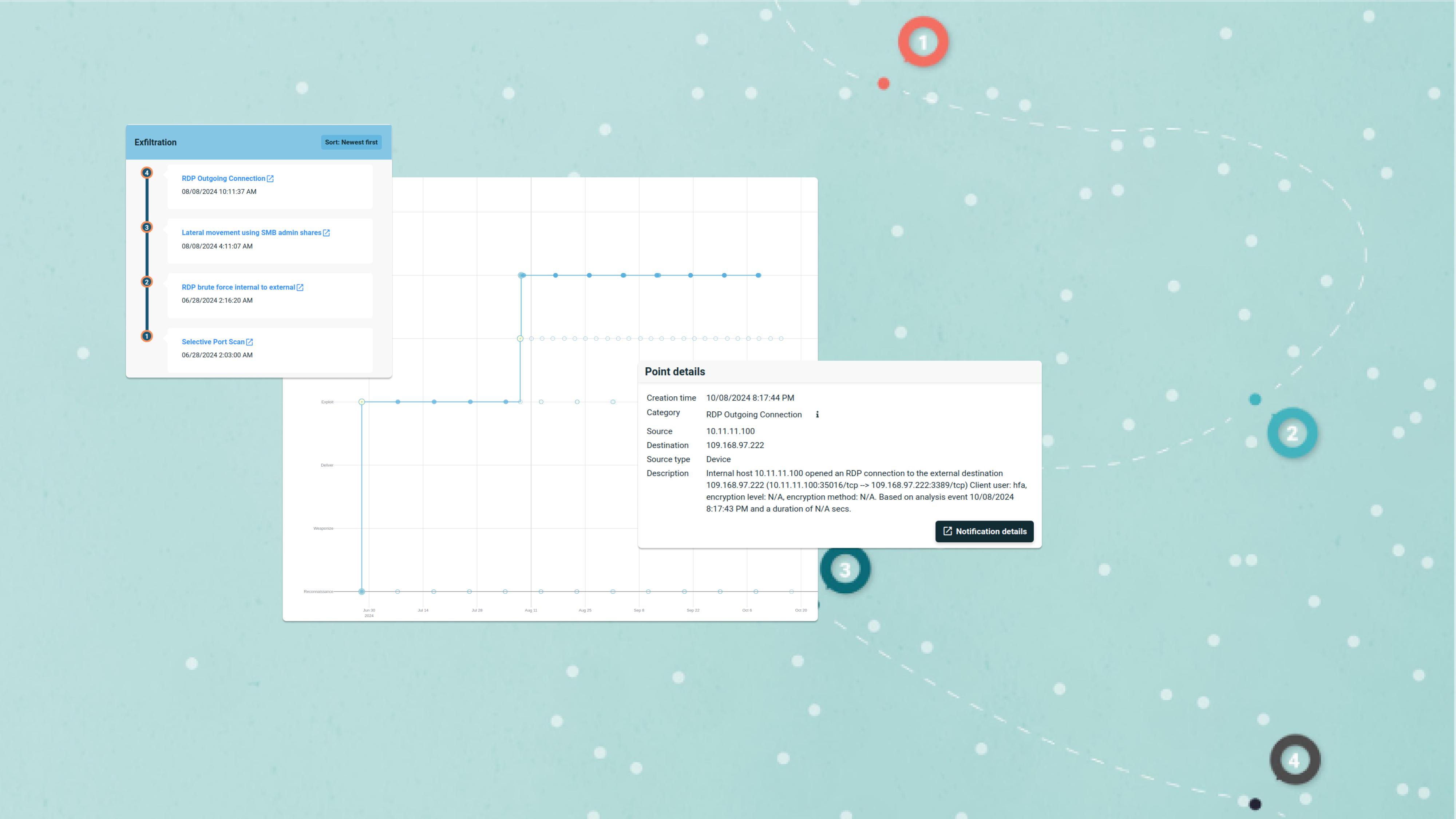
At this point it is old news, but this year NIS2 will finally move from being a theory to impacting everyday life of organizations, as Member States must transpose the Directive into applicable, national law by 17 October 2024. The European Directive requires Member States to adopt laws that will improve the cyberresilience of organizations within the EU and impacts organizations that are defined as “operators of essential services”. Under NIS 1, EU member states could still choose what this meant, but to ensure more consistent application, NIS2 has set out its own definition. Rather than making a distinction between operators of essential services and digital service providers, NIS2 defines a new list of the following sectors: